The Enterprise Security Architecture, Part 3
Image Source: Specops
I’ll just leave that image there so you can appreciate it’s profoundness…..
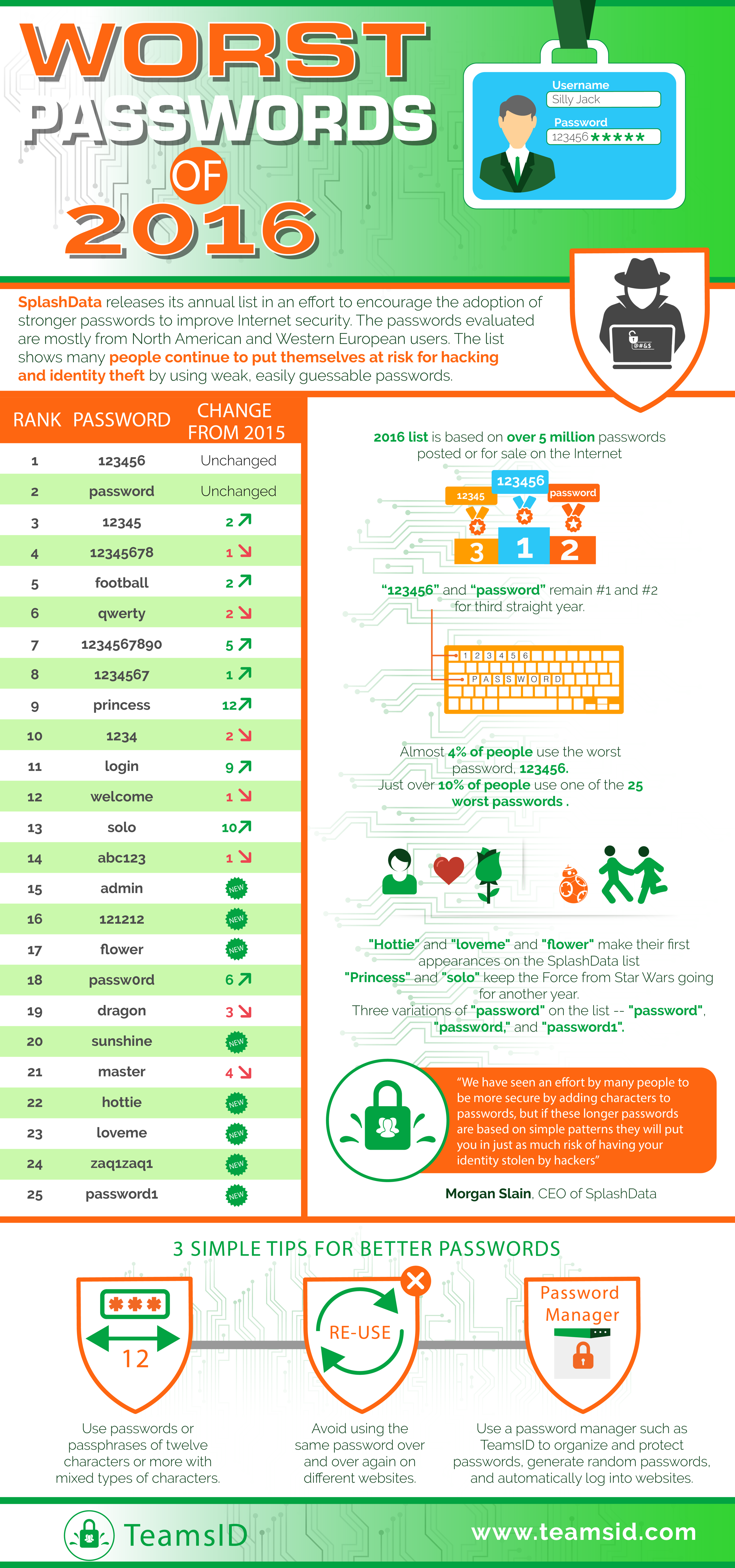
Any discussion about security needs to include our love/hate relationship with passwords. Passwords are one of the most basic security steps used in all aspects of cyber security. So why is it that there are so many people who have challenges with such a simple item? SplashData, a provider of password management tools, releases an annual list of the worst password people are actively using. This data comes from evaluation of leaked passwords from North America and Europe. This infographic is a little large, but I thought it worth viewing.
Image Source: TeamsID (SplashData)
So why do people have so many challenges with passwords? Specops, the source of the “underpants” photo above made this observation:
End users are wired to pick weak passwords – this goes back to cognitive psychology. As humans we are not equipped to retain meaningless information which means we make poor password choices. Either our passwords are just outright silly or they relate to our ego, our interests or something familiar. This is evident in the many common password lists out there, where password, 123456, football, master and monkey continue to make the top 20 most common passwords selected.
Instead of relying on end users to create secure passwords, which is unlikely, IT departments need to embrace better password policy practices that enforce more secure passwords by blocking the use of common dictionary words and enable more complex passwords by mixing different complexity rules (e.g. minimum of 10 characters with all four character sets or use passphrases that are longer than 20 characters).
This statement above regarding password complexity has been the standard operating procedure within IT and the business world for many years. Most of those practices originated back in the early 2000s from a document published by the National Institute of Standards and technology titled, “NIST Special Publication 800-63. Appendix A” (new 2017 version). We’ve all seen the standards that have been published with the “must contain at least 1 capital letter, 1 lowercase letter, 1 number and 1 special character.” And those passwords should be changed frequently.
Interestingly enough, the original author of the standard, Bill Burr, who is now retired, just recently was interviewed by the Wall Street Journal. In that interview, Burr admitted that he regretted his recommendations.
The problem is the advice ended up largely incorrect, Mr. Burr says. Change your password every 90 days? Most people make minor changes that are easy to guess, he laments. Changing Pa55word!1 to Pa55word!2 doesn’t keep the hackers at bay. Also off the mark: demanding a letter, number, uppercase letter and special character such as an exclamation point or question mark—a finger-twisting requirement.
In June, the NIST did a complete rewrite of the standard with a completely different set of recommendations. The goal was to make obscure passwords that are easy for the user to remember, but more challenging for hackers or bots to crack. Password expiration is no longer recommended unless there is evidence that your password was stolen.
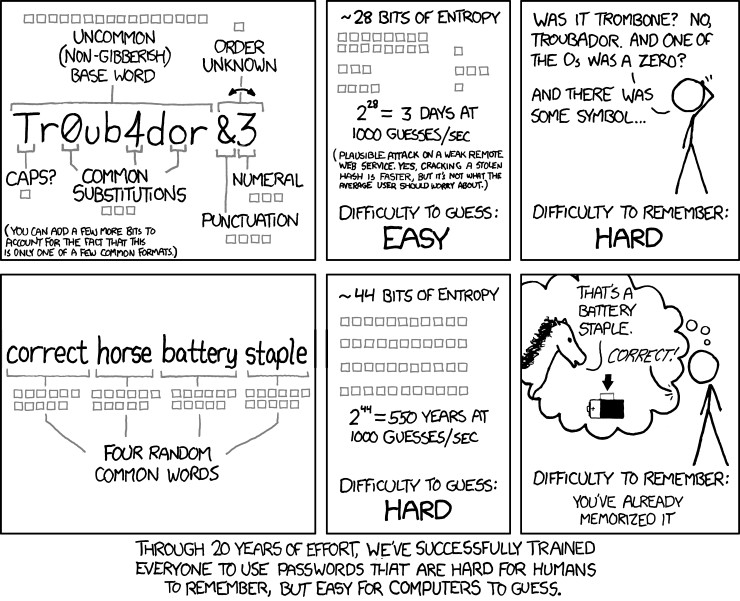
Back in 2011, this exact sentiment was expressed by cartoonist Randall Munroe, the author of the comic xkcd. “Through 20 years of effort, we have correctly trained everyone to use passwords that are hard for humans to remember, but easy for computers to guess.”
Now, how long will it be before this common sense change will filter out into the business world…?