Posts Tagged Part 2
Disruptive Technology & Trends for 2016 – 2018
Emerging Technologies, Innovations & Trends, Part 2
Image Source: Brian Solis
Let’s continue looking at the work of Brian Solis. One of Solis’ more interesting recent endeavors is to put together an annual list of what he considers to be the top Disruptive Technology Trends for the current year and forward. Here is his list for 2016-2018:
1) The New Brand: Experiences are More Important Than Products
Customer experiences become more important than products; companies now have to consider how products and services enhance specific lifestyles and workflows.
The legacy value of brands is overtaken by brands that earn relevance by investing in engagement and collaboration in moments of truth…beyond creative. Marketing becomes CX. This includes the sum of all disparate parts, marketing, product, sales, service, support, CRM, R&D, etc. Brands must also zero-in on the needs, values and aspirations of a generation that defines everything radically differently than previous generations.
2) Goodbye Sharing Economy, I Want My On-Demand Economy…Now!
Was there ever really a sharing economy if no one was actually sharing? The sharing economy officially dissolves: everything becomes on-demand and this forces economists and ultimately businesses to understand new markets and workforces that create alternative supply based on rising demand. On-demand companies and their ecosystems of workers and customers trade on the value of reputation + trust + value.
Beyond seeing the “Uber or Airbnb of everything,” new classes of services will rise and fall based on new behavior and expectations. I also refer to this movement as the “selfish” economy in that consumers will expect every business, even those that are traditional, to do business where transparency, immediacy and context reign supreme. Everything will be on-demand, including B2B services.
3) Digital Detox Improves Digital Productivity
Digital is its own drug. People will learn how to hack their workflow because they have to. There’s too much email, too many meetings and not enough leadership to change routines. This leads to the need for individual productivity hacks. These acts go beyond employee efficiency; they will improve experiences and relationships professionally and personally. Everyone will need some sort of digital detox and/or focus.
While some will simply unplug from the Internet, others will discover and share “life hacks” such as…
• Writing down distractions from tasks at hand
• Checking email once a week
• Scheduling meetings in 20-25 minute increments
• Listening to music without lyrics
• Spending 10 minutes a day on Headspace
• Fasting from media
• Not responding to every txt
• Turning off all desktop, social and mobile notifications
4) Every Company Undergoes Digital Transformation and Gains Empathy in the Process
Digital transformation – the re-alignment of, or new investment in, technology and business models to more effectively compete in a digital economy – becomes standard. Companies will invest in digital customer experiences to improve experiences for all customers and employees.
There is no one type of customer or employee. Thus, digital transformation efforts will not be informed by digital trends; instead, social science will help decision-makers better understand how digital trends affect how people work, shop, communicate, what they value etc. Technology will then be an enabler to human-centered transformation in the enterprise to create more adaptive models, processes and systems to evolve.
5) The Dynamic Customer Journey Changes Brand Dynamics
The customer journey decentralizes, becoming a series of non-linear mobile-centric micro-moments, mimicking everyday consumer activity and communication. This sets the stage for relevant brand and product serendipity.
For example, Google learned that 90% of smartphone users are not absolutely certain of the specific brand they want to buy when they begin looking for information online. And, 65% look for the most relevant information regardless of the company providing it. How companies become discoverable and how they lead customers through their journey requires a new marketing infrastructure to support a customer journey comprised of micro-moments. This means that legacy strategies are good only for yesterday’s customers. To reach mobile customers in each moment of truth requires new methodologies for search, advertising, content engagement, sales and support.
6) The Consumerization of Work Turn Employees into Collaborators
The consumerization of work goes beyond IT and devices; workflow, behavior and expectations mimic real-world apps like Snapchat, Uber, Tinder, etc.
Digital employees and customers think, act and expect differently. They want every business to feel, serve and work just like their favorite apps.
Enterprise software will start to mimic consumer apps and ultimately reshape the role of IT and the processes it manages to support employees. Slack is just the beginning of an enterprise renaissance that doesn’t just change tech – it changes how companies (and people) work.
7) Humans Need Not Apply for Old Jobs
The gap between expertise for the jobs of yesterday and tomorrow is widening. Everyone becomes students again. Yes – robots already are and will continue to automate workflow. Factories aside, intelligent devices are replacing people in front-line roles such as those at eateries, including Eatsa and McDonalds.
Traditional education no longer suffices as people are learning basic skillsets without understanding or knowing how they correlate to tomorrow’s careers. People will specialize in tasks that computers need humans to complete. Scholastic and workplace education will formalize computer-proof and computer-partnered careers and programs, and thus education becomes a constant.
8) The Age of Corporate Renaissance
Old ways give to new business models, processes and philosophies; disparate departments merge, uniting tech and complementary disciplines.
Marketing and IT work together rather than compete. CX, CRM and marketing form new experience teams.
CIOs realize the “I” stands for “innovation” and as such understand external/internal behavior to rethink how people and tech work together now and in the future.
Training and education become proactive to help modernize the workforce.
HR undergoes a renaissance to provide a workplace that is native to Millennials and up-and-coming Centennials.
9) Corporate Innovation Centers Displace or Complement R&D; The Maker Movement Becomes Threat or BFF to Incumbent Companies
Traditional R&D is no longer sufficient. Big companies invest in innovation centers: some aim to act like startups, others set out to partner with or acquire them, and some seek to lure people away from #startuplife.
Either way, innovation centers allow slow-moving, risk-averse companies to spark new ideas, experiment faster, fail faster and gain momentum to affect HQ and force change from the outside-in.
Some great innovation that cannot see the light of day within larger organizations will develop new markets, upset incumbents and either succeed solo or rollup into those companies that could not innovate.
The maker movement is “Shark Tank” for geeks and it doesn’t need judges to fund them; there’s Indiegogo, Gofundme, Kickstarter, et al. for that.
10) Culture Finally Gets Its Time in the Spotlight – Welcome to Culture 2.0
Culture is largely misunderstood and undervalued by the C-Suite today. It’s one of the reasons morale is at an all-time low. This will change because it has to. Employee engagement or the lack thereof creates a morale-busting “engagement gap”, giving way to an executive-level charter to invest in “culture 2.0”
11) Businesses Must Live by Radical Transparency to Gain Trust and Business of Customers
Businesses must also practice radical transparency or risk irrelevance. Customers want to do business with companies that match their beliefs and values. Customers are more aware and informed now. This means businesses must run counter to its normal practices, change and communicate this vision and changes in everything. With a more plugged-in understanding of human nature, businesses will not only create a happier and more productive culture: they will benefit from empowered employees, leading to an internal renaissance that yields new and innovative products, services, processes, and more.
12) Schools Pay Students to Learn and Become Agencies that Connect Companies with Expertise
The race for technical talent extends to Africa and other non-traditional establishments (such as prisons, etc.) to train qualified students computer and engineering sciences. Specialized schools will identify and teach students – even pay them to learn – and become an IP lab for companies to employ, similar to how outsourcing of other business functions works today.
13) Jarvis is Your New Chat Buddy and He Ushers in a Dawn of Conversational Commerce
Chatbots (and a dash of human interaction) turn messaging into concierge services (aka virtual assistants) and eventually predictive services that simplify everything from search to shopping to travel to customer service.
This sets the foundation for “conversational commerce.” The ability to buy products and order services without leaving the chat window becomes the new norm for everyday shopping, much like Amazon has become the standard for e-commerce.
Intelligent attendants such as Microsoft Cortana, Google Now, Amazon Alexa and Apple Siri will become staples in how people navigate life and work. Very soon, the complicated and often silly questions you ask of Alexa and Siri, will be answered.
You’ll be taken aback for a split second and then you’ll go on as if you couldn’t have lived without it.
14) Mobile-first Behavior Transforms the Web
The entire Web will be re-imagined for a mobile-first and mobile-only world that is screen, location, context and intention-aware. This radically transforms the purpose of the web to become more dynamic, personal and useful at a time when people are forcing the end of a traditional information-broadcast, page/form-based, keyword world. Everything from websites to apps to commerce will require overhaul or complete innovation to cater to the EGOsystem, or the demand for real-time personalized engagement.
15) The New @Machine Age Discovers the Fountain of Sleuth
Quantum computing dramatically accelerates the artificial intelligence race, applying machine calculations that are 100 million times as fast as today’s machines. IBM’s Watson is being applied to healthcare, finance and even cooking, to explore new solutions in cognitive computing. AI can sort through and assess information that humans may have missed or never considered. This type of work is already leading to new treatments, products, services, and yes, recipes. You can bet it will also be applied to call center technology and may or may not make you want to use counter services such as @service in response.
Artificial intelligence is just one area that will benefit from experimentation. Machine learning will also yield innovation in pattern recognition, predictive analysis, mimicked common sense, and even new ways to compute and solve problems.
More immediately though, breakthroughs in programming will eventually iterate and innovate existing engineering issues, air traffic control, curing diseases, etc.
16) Reactive Medicine Gets Proactive
Regenerative medicine cuts through the ethics debate by helping everyone gain access to cloneable organs.
Nanobots will be able to assess and fix us from within. Those made from our own DNA will eventually help cure us from deadly diseases ranging from blocked arteries to cancer.
Healthcare and athletic brands will also learn from Disney’s massive Magicband investment to bring big data insights to improve health and life experiences as part of a Human Operating System (Human OS). A human operating system becomes a platform for innovation that mimics the Apple product and iCloud universe. A Magicband-like device and other products designed to work in its ecosystem are constantly plugged into personal clouds accessible by healthcare providers. Blood, oxygen, vitals and more will shift the practice of medicine from reactive to proactive care.
17) The Sh#tshow that is The Internet of Things Finally Plugs into the Human OS
The Internet of Things becomes the Internet of Sh#t because it’s a mess with too many products and apps competing for consumer attention. This creates confusion and chaos as devices are proprietary, capabilities are too narrow and not reflective of everyday life and only a few companies such as Google’s Nest and Apple’s Homekit are designing plug-and-play smart ecosystems. Even still, technology must be invisible and interoperable.
Developers must plug into the Human Algorithm and the Human OS, envisioning the body and critical activities as an ecosystem/platform rather than technology and device-first products.
On the immediate horizon, smart connected products (The Internet of Things) will help consumers in transparent means, such as in-product communication, where products communicate to manufacturers, users and suppliers about state, maintenance needs and updates. This will be done in-home and also onsite where locations become smart about visitors to better guide experiences.
18) Live! Streaming! Mobile! Video! Now!
Live streaming (video) continues to bring niche moments to life, interrupting streams everywhere, making conversations on demand a form of engagement and entertainment. This makes everyday activities such as gaming, sports, concerts, events, TV, discussions, etc., become content and its hosts and participants the new weblebrities. This puts pressure on Youtube, Vine, Facebook, Snapchat to rethink video algorithms and subsequently monetization/advertising platforms. With streaming services forcing the unbundling of traditional subscription channels and the democratization of content production and distribution, consumers re-define programmatic content and reshape the definition of “TV.”
19) Say Hello To My Little Mends; Drones Join the Workforce
Drones will continue to revolutionize photography and videography but real innovation will derive from utility in vertical applications such as delivery, care, exploration, etc.
20) Ctrl-P: Print Solutions at Will
The proliferation of 3D printing solves problems and creates solutions in vertical industries (healthcare, aerospace, automotive, manufacturing, etc.), disrupting supply chains as it matures.
Personal applications will initially be served by brick and mortar establishments such as home improvement, auto repair, and other services where parts take time, are too expensive or unobtainable.
21) Siri, Take The Wheel
You may already own your last car. Autonomous vehicles will start to make their way onto public roads as laws rapidly iterate to make way for the inevitable. v1.0 will be very beta, with initial cars shipping with steering wheels and requiring drivers to “take a back seat” but be ready to take over at a moment’s notice. Fully autonomous, self-driving cars will be on the road by 2025. Cars will learn not only how to drive, but also how to limit or strategically consider accidents, injuries and even death of passengers, drivers and pedestrians.
Intelligent transportation not only changes how people, goods, etc., get from point A to point B, but also how vehicles and technology talk to one another to create safer passage ways. Each will also transform regulation to expedite a connected grid where transportation engineering and infrastructures as well as vehicles, gear, components, etc. work together.
22) Experiences Get Real Virtual
Oculus, Hololens, MagicLeap are bringing the virtual world to life. Immersive computing will find its niche beyond industrial design and start to permeate high-end gaming and other experiential sectors. It will open up an entirely new world that truly brings VR/AR alive…or closer to lifelike.
VR/AR are already a given. As gear becomes increasingly portable (think something like Google Glass), though, experience architects and next-gen imaging equipment will design immersive 360-degree experiences that don’t just replicate everyday life, but instead enhance and even challenge it. Think about shopping with products and attendants that appear out of nowhere, or information about products that come to life as you pick them up. When you visit Hawaii and the land where Jurassic Park was filmed, you will have the opportunity to actually visit Jurassic Park. Playing games where the field of play is your physical environment with challenges greeting you in your own space. Total Recall and Minority Report are just around the corner.
23) Power On…ward
In-home battery systems provide an entry-level solar solution to those with electric cars. Systems such as Tesla’s Powerwall and Powerpack lead to a battery innovation race that benefits households, devices/appliances and other goods powered by less eco-friendly means and the greater power sector.
24) Fashion Sense Gets Smart, Darlings
Intelligent or smart fabrics (E-textiles) make clothes more than fashionable or useful: they become part of a new genre in the wearable movement. Working together, many types of sensors integrated into one larger garment can tell different stories and unlock new possibilities.
Clothes will have beacon-like technology to control/inform surroundings. Clothing articles will transform based on environment and activities, and also sustain desired body temperatures.
Through Bluetooth technology, clothing will communicate body status to core devices that track performance, state, etc. for you and your healthcare provider.
25) Finance Gets a Makeover Inside and Out
The blockchain allows you to create a public ledger system that’s accessible for all, and secure. Blockchain technology will influence global financial organizations to rethink banking infrastructures. Rather than transacting based on the individual, currency and ultimately goods become individual assets. Each transaction becomes a micro-purchase around your account, but it doesn’t actually involve your personal authentication. Authentication is performed by your assets. All of this is recorded on your bank’s open blockchain ledger in real-time, easily and inexpensively.
Speaking of banks…based on the rise of the “selfish economy” and the consumerization of all tech, the idea of what a bank is and how people interact with it creates new micro-banks that look, act and perform banking functions for a digital/mobile generation.
26) The Cloud Takes Over Business
Critical ERP systems beyond CRM, marketing, etc. move to the cloud. Businesses cannot compete at the speed of digital Darwinism if they don’t change how they “do” business.
Nearly a third of all enterprise resource planning (ERP) systems in the world will attempt the migration to the cloud in the next two years.
I found a number of these very interesting due to personal experience as well observation of some of these trends first hand.
3. Digital Detox Improves Digital Productivity – I have observed a greater number of friends & acquaintances who have started regularly disconnecting from digital media. For myself, I have actively used a couple of the “life hacks” mentioned such as “Spending 10 minutes a day on Headspace” & “Listening to music without lyrics”. Both of these actions appear to have increased my concentration level while I am engaged in either work or study.
14. Mobile-first Behavior Transforms the Web – The trend towards “Mobile-first” behavior on the web has been rapidly growing since the time this article was written. At times, this can be unfortunate for the end user as many companies have attempted to migrate to a “mobile-first” approach without real consideration if there was an actual need.
24. Fashion Sense Gets Smart, Darlings – As existing types of wearables have gotten more and more popular, there are new types of wearbles rapidly being developed in the market as well. I am expecting to see sensors integrated into clothing within the next year due to collaboration between a fitness wearable maker and a sports clothing manufacturer.
26. The Cloud Takes Over Business – As cloud hosting has come down in costs, it’s only natural that businesses will start looking at it more seriously. Even though the economy has recovered somewhat in the last few years, this has not stopped companies from looking for additional ways to reduce local costs and outsourcing the physical IT hardware resources is a very attractive opportunity. In all reality, most companies have nothing to really lose from such a transition.
It will be interesting to see over the next year, how many more of these trends continue to progress and become mainstream.
Architectural Challenges
The Enterprise Business Architecture, Part 2
Image Source: DesignBoom
Architectural Photographer and Artist, Filip Dujardin, has a special talent. He can create images such as the photo above, which, at first glance, appear unusual yet somewhat plausible. Upon careful inspection, though, these buildings are actually impossible. He is able to take multiple digital elements and create these surreal buildings. According to Dujardin, “the building becomes real if the shadows are well done.”
So what does that have to do with Business Architecture?
The fact is that many organizations claim to have setup an Enterprise Architecture including the Business Architecture viewpoint, but in reality it’s just on paper. It’s not real..!!! Even if the organization claims to have been successful, there is no tangible benefit that is being realized. In fact, roughly 2/3 of all EA initiatives are considered to have failed.
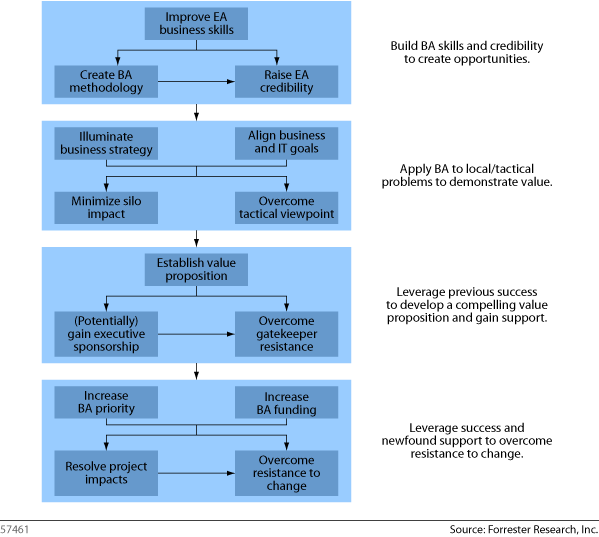
Specifically in the Business Architecture arena, only a small percentage of programs are actually delivering value back to the organization. Forrester published a report in 2010 listing the top 14 Business Architecture Challenges and some recommendations on how to overcome those challenges. Instead of regurgitating what author Jeff Scott wrote, I think his article stands on it’s own (Scott, 2010):
Fourteen Business Architecture Challenges And How To Overcome Them
EAs Are Challenged By Their Own Business Architecture Capabilities
Though business architecture has been part of the basic EA model from its inception, only in recent years have EAs focused there. Business architecture knowledge, skills, and methodology are all lagging general EA by a decade or more, and because business architecture is fundamentally different from technology architecture, the learning curve is very steep. The good news is that EA teams can overcome these challenges without much help or support from the rest of the organization. The following challenges are within EA’s scope to resolve:
- Weak EA business skills. Most EA teams are composed of some of the organization’s strongest technologists. Their past experience, interest, and current EA roles keep them overly focused on technology topics with little time — and often little inclination — to improve their business and business architecture knowledge. Successful business architects are allocating time to read business books, interact with business mentors, and learn about the fundamentals of their company’s business model. Non-IT-based business architects come to the table with M.B.A.s and business-specific experience.
- A low level of EA credibility in the business. Fifty-four percent of EA teams report to a senior-level executive such as a CIO or CTO, while the rest report lower in the IT organization. With little business visibility, many aspiring business architects are virtually unknown to business leaders. In addition, many EA teams have unintentionally created a negative impression through their efforts to hold project teams to architectural standards. Successful EA teams position the EA practice as a project resource as opposed to a controlling function, thereby turning their IT peers into business architecture (BA) advocates who promote them to the business.
- A lack of industry-standard business architecture methodology. Business architecture is still in its infancy. While there are a number of “meta methodologies” in the public domain, they are neither comprehensive nor robust. Business architects are still experimenting with which approaches work best. For the foreseeable future, business architects will have to craft their methodology from what is available and continue to evolve it over time.
- Poorly articulated business strategy. Many architects might disagree that this is an EA team issue, but Forrester believes it is a core responsibility of the business architect to identify, clarify, and document business intent. Business leaders are skeptical of the value of a documented business strategy because they have rarely seen a good one. Often architects address this challenge informally, gaining small wins with the business before tackling an enterprise view. Architects that create a well-articulated view of business strategy report an “aha” reaction from their business executives.
- Weak business-IT alignment. Contributing to many EA teams’ lack of business credibility is the fact that they reside in an IT organization that is poorly aligned with business goals. Architects take one of two opposing strategies to overcome this challenge. One is to meet it head-on and apply EA and business architecture specifically to helping improve alignment. The other is to distance EA from the IT culture to present a different viewpoint to the business.
EAs Are Challenged By The Business Culture That Surrounds Them
While BAs are still trying to figure out what a really great business architecture looks like, they are facing an even bigger challenge in connecting with organizations that are not designed or predisposed to work in a coordinated, strategic fashion. The organization and cultural challenges BAs face are:
- IT gatekeepers who prevent EA’s interaction with the business. Most IT organizations have established business relationship managers as a formal or informal role. Whether they are project managers or senior IT executives, they play an important role in managing the business relationship by providing a single point of contact and by isolating the business from many of the day-to-day nuances of managing IT. Strong gatekeepers create a formidable challenge to EA, and successful architects most often partner with them as opposed to try to circumvent them.
- Organizational silos that make it difficult to get the big picture. Business unit independence is the norm and is a natural occurrence spawned by dealing with span of control challenges. Successful business architects use this to their advantage by cultivating a relationship with one business unit and leveraging success there to gain access to others.
- A tactical business focus. Quarterly financial reporting, a lack of corporate strategic thinking, and the fast pace of business environment change drive short-term business thinking. Convincing business leaders to explore a strategic viewpoint is challenging. Successful approaches to this challenge usually begin with finding a specific problem business architecture can solve as opposed to trying to sell the larger concept.
- A culture of change resistance. Almost all organizations resist change unless their business model is based on product innovation. Resistance to change is a very powerful force, as it is usually rooted within each individual’s perspective of what he or she has to do to be successful. Resistance to change can rarely be “solved” but instead must be managed. Architects who manage change well first develop a plan to understand the factors that are creating resistance and then attack those issues by lowering the perceived risk of doing something different.
EAs Are Challenged By Lack Of Support And Resources
Architects can’t build business architecture in a vacuum. They need the support, or at least the attention, of a number of businesspeople at various levels of the organization. Most business architecture efforts are small and only require minimal funding; however, like any other initiative, they do need money — and the more they have, the faster they can proceed. Developing a clear value proposition can be the most challenging aspect of building business architecture. The resource and support challenges BAs face are:
- Business architecture has yet to establish a compelling value proposition. Business architecture is still relatively new; few companies are far enough along the path to report the value they are receiving. As with other EA domains, BA value is hard to specify until architects do enough work to show results. Current BA approaches that are showing results typically focus on specific problems or a single business unit.
- Business architecture rarely has executive sponsorship. Though many architects list executive sponsorship as a critical success factor (CSF), few are reporting that they have it. Securing sponsorship is somewhat of a “chicken and the egg” problem. Architects want sponsorship to drive support for BA but generally have to make enough progress to demonstrate value to gain sponsorship. Architects that do gain executive sponsorship typically first show results at a project or departmental level.
- EA teams rarely have specific business architecture funding. Without a clear and compelling value proposition, most EA teams find that BA funding is limited. Many have made the case to hire a single business architect to round out the EA team, but few have established funding for specific BA initiatives. Successful BA startup efforts leverage a small number of resources to manage a larger number of non-EA participants.
- Availability of business resources is low. Business executive and senior management time is a scarce commodity. Most business managers are overworked, often finding themselves with a full calendar of meetings most days. Consequently, they are very careful about committing the little free time they have. Executive sponsorship can overcome this challenge, but most BAs are forced to work at a lower level with the intent to move up in the organization as they produce results.
- Strategic activities have low priority. Most organizations are tactically focused with little appreciation of the strategic value of architecture and strategy. Most business managers are accustomed to seeing strategy efforts as a waste-of-time planning exercise. BAs report making headway when they judiciously apply strategic tools to help solve current problems.
The Solution is in the Connection of the Challenges
Taken individually, these challenges can seem overwhelming, but this is a problem of not seeing the forest for the trees. Putting the challenges in context creates a clear picture of how to proceed (see figure below). To tame these BA challenges:
- Assess the challenges you face. Not all business architects will face all 14 challenges, nor will each challenge present the same level of difficulty. Lay out the challenges in road map form that clarifies your business architecture effort’s current position and indicates future steps. Focus your attention and energy on the next challenge you need to address.
- Build foundational success first. Though the solutions are not completely as sequential as Figure 3 indicates, building a strong foundation is crucial to achieving long-term success. In general, executive sponsorship and funding can only be solved when you have a compelling value proposition, which you can only create once you have demonstrated value in some way, which you can only do when you have the right skills and capabilities. Attempting to skip steps will only lead to frustration and additional work to recover lost ground.
- Demonstrate value to overcome organizational challenges. Organizations will rarely get behind a BA initiative because it is the right thing to do. Everyone wants to know “what’s in it for me?” Find opportunities to add value to build up credibility. Typical places business architects are getting early traction are in business transformation projects, business-IT alignment initiatives, annual IT and business planning exercises, merger and acquisition activities, and large process improvement initiatives.
References:
Scott, Jeff. (2010). Fourteen Business Architecture Challenges And How To Overcome Them. Forrester. Retrieved October 30, 2017 from https://www.forrester.com/report/Fourteen+Business+Architecture+Challenges+And+How+To+Overcome+Them/-/E-RES57461
Effective Security Measures
The Enterprise Security Architecture, Part 2
An XT-4200 Post & Beam Gate providing a vehicle security access point (American Security Today)
So how do we go about creating the Security Architecture? What needs to be included and how do we measure its’ effectiveness? One thing is clear. The security of yesterday is no longer adequate for the risks of today.
In March of this year, the Ponemon Institute released a study named “The Need for a New IT Security Architecture“. The report surveyed more than 4000 IT and security experts from around the world. An analysis of this report by security firm Centrify discussed the findings that concern risks created by cyber-crime, employee negligence and organizational dysfunction and the technologies respondents believe are most effective at dealing with these risks (Gibson, 2017):
Outdated Security Solutions
Organizations are concerned they will not be able to manage emerging risks because of outdated security solutions.
- 69 percent of respondents say their organization’s existing security solutions are outdated and inadequate.
- What is needed, according to 74 percent of respondents, is a new IT security framework to improve security posture and reduce risk.
- A new strategy is important in order to manage potential risks from the Internet of Things (75 percent of respondents).
Trends in IT Security Risk
The findings reveal that most risks, with the exception of globalization of the workforce, are very significant. The top cybercrime risks are:
- Nation state attackers (80 percent of respondents)
- Breaches involving high-value information such intellectual property and trade secrets (79 percent of respondents)
- Malicious or criminal insiders (76 percent of respondents)
- Cyber warfare or cyber terrorism (76 percent of respondents)
An Evolving Workplace
The workplace is changing and so are the human factor risks. While 81 percent of respondents are concerned about the inability to hire and retain security staff with knowledge and credential, employee behaviors are creating risks that pose a significant risk.
- Employee complacency about security (74 percent of respondents)
- Lack of employee awareness of security practices (72 percent of respondents)
- The inability to control employees’ devices and apps (71 percent of respondents)
Complexity and legacy drag is a familiar problem that leads to high cost and contributes to shortage of competent professionals. Complexity and outdated security architectures create risk and weaken security posture.
Complexity is a Security Risk
Complexity of business and IT operations is a significant security risk. According to 83 percent of respondents, too much complexity is making organizations more vulnerable to security threats. Other trends are the growth of data assets (78 percent of respondents) and the process of integrating third parties into internal networks and applications.
Complexity is created in part by security vendors, who for decades have sold point solutions into IT environments with little thought to integration, maintenance and the cost of expertise to maintain their products.
Important Technologies for IT
Certain technologies are needed for a new IT security infrastructure.
Respondents believe their organizations’ IT security solutions are outdated and failing to mitigate the risks of cyber-crime, employee behavior and organizational problems. The most important technologies are:
- Identity & access management (78 percent of respondents)
- Machine learning (77 percent of respondents)
- Configuration & log management (76 percent of respondents)
An Architecture to Secure Identity in a Boundaryless Hybrid Environment
As reflected in the concerns of survey respondents, aging security infrastructure and point products create complexity, increase cost and risk and contribute to the critical security staff shortages. New security architectures that protect digital identity of all users across boundary-less hybrid environments and myriad devices are required.
We know, according to Verizon’s 2016 Data Breach Investigations Report, that the #1 cause of data breach is compromised user identity. We know that eliminating multiple identities and passwords, combined with least-access least-privilege policy and multi-factor authentication (MFA) everywhere is one effective way to contain and prevent attackers from gaining access to critical resources.
So with all these concerns, what are the necessary elements in a contemporary Security Architecture that not only protects users and applications, but improves productivity and security? According to Gibson, they can be summarized as:
- A modern security architecture is purpose-built, based on a goal to protect digital identity for all users across hybrid cloud and mobile environments.
- It’s built on a single code-base, with API’s SDKS’s that support security industry standards and integrates with other technologies.
- It’s constantly evolving.
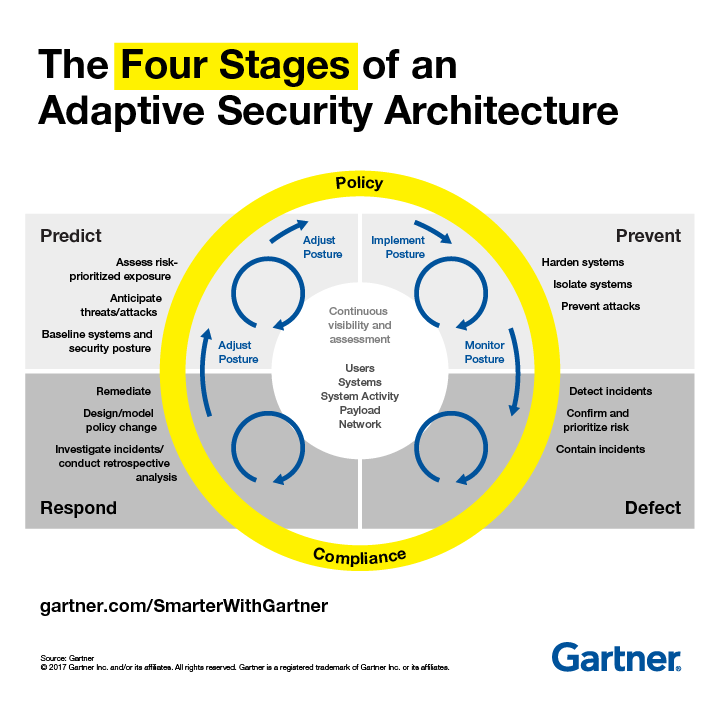
Rob van der Meulen of Gartner also recently posted a similar conclusion in a security article titled “Build Adaptive Security Architecture Into Your Organization“.
Many enterprise IT security teams spend much of their time focused on preventing a cyberattack. In doing so, they have implemented a “incident response” mindset rather than a “continuous response” where systems are assumed to be compromised and require continuous monitoring and remediation.
The adaptive security architecture is a useful framework to help organisations classify existing and potential security investments to ensure that there is a balanced approach to security investments. Rather than allowing the “hot” security startup of the day to define security investments, Gartner recommends that security organizations evaluate their existing investments and competencies to determine where they are deficient.
Digital business is built upon an intelligent mesh of devices, software, processes and people. This means an ever more complex world for security, demanding a continuous, contextual and coordinated approach.
The article went on to describe 4 stages of this new “Adaptive Security Architecture”
This concept of continuous improvement and adaptation is not new in the business world. Applying similar principles to a Security Architecture has rapidly evolved into the only way to stay on top of the ever changing world of today’s security risks.
References:
Gibson, Mark. (February, 2017). Ponemon 2017 Report: The Need for a New IT Security Architecture. Centrify. Retrieved October, 13, 2017 from https://blog.centrify.com/ponemon-2017-report/
Welcome to the Virtual World…
The Enterprise Technology Architecture, Part 2
There are many times when we have certain expectations, and yet reality proves to be something different than expected. Case in point, the image above shows us an expectation of a “virtual world” based on the 1999 movie, The Matrix, in contrast with an example of the recent personal virtual reality technology. What we expected (or hoped for) is not what we got. In the same way, this blog entry is not about virtual reality, but a discussion about system virtualization.
There is no spoon….
In general, virtualization refers to the technology that creates a logical (virtual) system instead of a physical system, specifically in the field of computer hardware. This hardware can be servers, storage devices, or even network resources. This practice started in a primitive form back in the 1960s on mainframe computers, but has gradually increased in scope and capabilities and is a mainstream technology used today. In a simple breakdown, virtualization falls into the following categories:
- Platform/Hardware virtualization – A full virtual machine acts as a real computer with it’s own operating system.
- Desktop virtualization – A logical desktop which can run on any physical client while processing takes place on a separate host system.
- Application Virtualization – An application runs off a client machine, but in reality is being hosted on larger system which typically has greater processing power.
Interestingly enough, this has a direct correlation to the different service types provided in the cloud-computing environments, as I talked about a number of weeks ago in Let’s get Saassy.
- SaaS – Software as a Service: The capability provided to the consumer is to use the provider’s applications running on a cloud infrastructure. The applications are accessible from various client devices through either a thin client interface, such as a web browser (e.g., web-based email), or a program interface. The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, storage, or even individual application capabilities, with the possible exception of limited user-specific application configuration settings.
- PaaS – Platform as a Service: The capability provided to the consumer is to deploy onto the cloud infrastructure consumer-created or acquired applications created using programming languages, libraries, services, and tools supported by the provider. The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, or storage, but has control over the deployed applications and possibly configuration settings for the application-hosting environment.
- IaaS – Infrastructure as a Service: The capability provided to the consumer is to provision processing, storage, networks, and other fundamental computing resources where the consumer is able to deploy and run arbitrary software, which can include operating systems and applications. The consumer does not manage or control the underlying cloud infrastructure but has control over operating systems, storage, and deployed applications; and possibly limited control of select networking components (e.g., host firewalls).
This direct correlation is due to the fact that most cloud computing technology heavily relies on virtualization to function. “Virtualization is a foundational element of cloud computing and helps deliver on the value of cloud computing. While cloud computing is the delivery of shared computing resources, software or data — as a service and on-demand through the Internet” (Angeles, 2014).
So how does virtualization tie back into Enterprise Technology architecture and Enterprise Architecture in general?
In response to a question regarding the impact of virtualization and cloud computing on Enterprise Architecture, John Zachman (2011), creator of the Zachman Framework, stated:
The whole idea of Enterprise Architecture is to enable the Enterprise to address orders of magnitude increases in complexity and orders of magnitude increases in the rate of change. Therefore, if you have Enterprise Architecture, and if you have made that Enterprise Architecture explicit, and if you have designed it correctly, you should be able to change the Enterprise and/or its formalisms (that is, its systems, manual or automated) with minimum time, minimum disruption and minimum cost.
Adrian Grigoriu, author of An Enterprise Architecture Development Framework, further expounded on the benefits virtualization brings to Enterprise Architecture (2008).
In this fast moving world, the business of an Enterprise, its logic, should not depend on IT technology, that is what it is or its implementation. Business activities should be performed regardless of technology and free from tomorrow’s new IT hype. Why be concerned whether it is mainframe, COBOL, JavaEE or .NET, Smalltalk, 4GL or AS400 RPG! At the same cost/performance level, IT should decide technology realizing that ongoing change is inevitable.
Business should be willing to adopt technology virtualization to be able to interact with IT technology at a service level, where the negotiation between business and IT is performed in a communication language structured in terms of capabilities, relative feature merits, and their cost. IT functional and non-functional capabilities will be delivered under SLAs at an agreed price. IT virtualization adds an interface layer hiding the IT implementation complexity and technology, while bridging the divide between business and IT.
Even back in 2008 and 2011, Enterprise Architecture leaders realized the benefits that could be gained from virtualization. Considering the growth of the technology since then, the benefits have exponentially multiplied. EA ultimately relies on technology itself to be efficient, therefore, technology that allows for rapid changes will always be of primary importance. In addition, virtualization brings reduced complexity, lowered costs, simplified IT management, improved security and flexible IT service delivery to the organization. These benefits not only help EA, but IT and the organization in general.
References:
Angeles, Susan. (2014). Virtualization vs. Could Computing: What’s the Difference? Business News Daily. Retrieved from http://www.businessnewsdaily.com/5791-virtualization-vs-cloud-computing.html
Zachman, John. (2011). Cloud Computing and Enterprise Architecture. Zachman Internaltional. Retrieved from https://www.zachman.com/ea-articles-reference/55-cloud-computing-and-enterprise-architecture-by-john-a-zachman
Grigoriu, Adrian. (2008). The Virtualization of the Enterprise. BPTrends. Retrieved from http://www.bptrends.com/the-virtualization-of-the-enterprise/
Taming the Beast
The Enterprise Data Architecture, Part 2
So we know that Big data is a big problem. What can we do about it and what can we do with it?
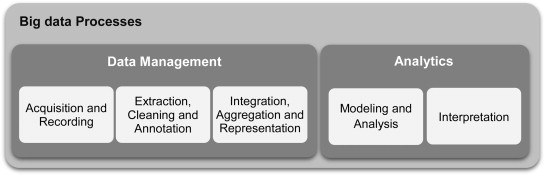
First of all, we need to have an understanding of the content of the big data and how we process this information. Gandomi & Haider (2015) state that “the over all process of extracting insights from big data can be broken down into five stages. These five stages form the two main sub-processes: data management and analytics. Data management involves processes and supporting technologies to acquire and store data and to prepare and retrieve it for analysis. Analytics, on the other hand, refers to techniques used to analyze and acquire intelligence from big data.”
Image source: Gandomi & Haider, 2015
Once we have a better understanding of the how to process Big Data, how can we efficiently leverage the information we gain?
The growth of data metrics over time in both quantity and quality is nothing new. Even in the 80s and 90s, articles were published regarding the exponential growth of data and the challenges caused by this growth (Press, 2013). The challenge that has been continually fought in all those years has been to make the available data meaningful. Big data, as we have defined it, provides many opportunities for organizations through “improved operational excellence, a better understanding of customer relations, improved risk management and new ways to drive business innovation. The business value is clear” (Buytendijk & Oestreich, 2016). Yet, investment in big data tools and initiatives are slow to materialize.
Organizations can incorporate big data initiatives into their existing business process components and artifacts. This will help establish big data as part of their Enterprise Architecture Implementation Plan and incorporate these new business strategies into the future architecture. Educating business leaders and stakeholders as to the benefits of big data initiatives will help overcome any concerns they may have (Albright, Miller & Velumani, 2016). Back in 2013, Gartner conducted a study on Big Data which showed that many leading organizations had already adopted big data initiatives to various degrees, and were starting to use the results in both innovation initiatives as well as sources of business strategy. Included in their results from that study, they found that “42% of them are developing new products and business models, while 23% are monetizing their information directly” (Walker, 2014).
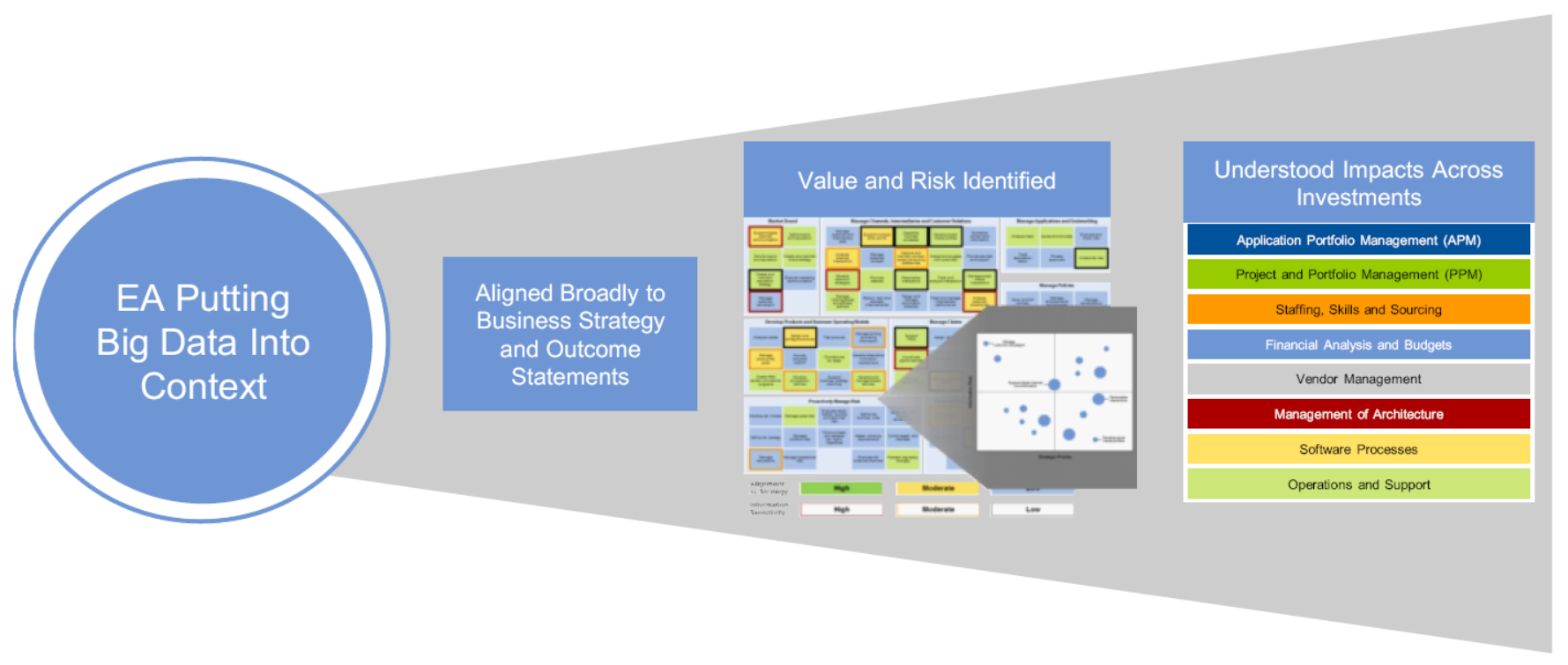
This is where Enterprise Architecture comes into play. EA is uniquely equipped, with it’s holistic view of strategy, business and technology, to not only create a strategic plan to address the potential big data opportunities, but to create a road map which positions organizations to improve operations, enable growth, and foster innovation. “Organizations that leverage EA in their big data initiatives are able to identify strategic business goals and priorities, reduce risk and maximize business value” (Walker, 2014).
Image source: Walker, 2014
Through the various efforts of EA, new technologies and new approaches to processing, storing and analyzing Big Data, organizations are gradually finding ways to uncover valuable insights. Obviously, leading the charge are leaders such as Facebook, LinkedIn and Amazon, but many other companies have joined the effort as well. “From marketing campaign analysis and social graph analysis to network monitoring, fraud detection and risk modeling, there’s unquestionably a Big Data use case out there with your company’s name on it” (Wikibon. 2012). This infographic below was put together by Wikibon to show how various business leaders have overcome their challenges and have tamed the Big Data beast.
References:
Albright, R., Miller, S. & Velumani, M. (August 2016). Internet of Things & Big Data. EA872, World Campus. Penn State University.
Buytendijk, F. & Oestreich, T. (2016) Organizing for Big Data Through Better Process and Governance. (G00274498). Gartner.
Gandomi, A. & Haider, M. (2015). Beyond the Hype: Big data concepts, methods, and analytics, International Journal of Information Management, Volume 35, Issue 2, April 2015, Pages 137-144, ISSN 0268-4012, http://dx.doi.org/10.1016/j.ijinfomgt.2014.10.007.
Press, G. (2013) A Very Short History of Big Data. Retrieved from http://www.forbes.com/sites/gilpress/2013/05/09/a-very-short-history-of-big-data/#1a7787af55da
Walker, M. (2014). Best Practices for Successfully Leveraging Enterprise Architecture in Big Data Initiatives (G00267056). Gartner.
Wikibon. (2012). Taming Big Data. Wikibon. Retrieved September 20, 2017 from https://wikibon.com/taming-big-data-a-big-data-infographic/