Posts Tagged Part 3
Insert Coin to Continue…
Emerging Technologies, Innovations & Trends, Part 3
So we’ve finally reached this mystical place known as the last blog post of the class…
We started the semester by discussing the impact of Digital Disruptions, explored the five different aspects of the Enterprise Architecture stack, and ended here, discussing Emerging Technologies and Trends. So we know the impact (the disruptions) that new technologies and trends can have on our organization. What tools and methods are available to help us decide if the disruption is worthwhile? If our organization
CIO Insight offered these 4 tips:
- Establish an emerging technology evaluation process that helps CIOs adopt only those technologies that will have a positive business impact. Evaluations should ask the questions: What does the company hope to achieve, and how will the hardware or application help meet that goal?
- Don’t get overly enamored of new technologies and applications without first looking at how the products might apply to the organization and its business needs. It sounds obvious enough, but many companies have gotten burned investing in products that were hyped by vendors although they weren’t well-suited for their needs, budget, IT infrastructure, culture, etc.
- When deciding on a new technology investment, don’t rely on intuition to make the call. Also, don’t make the decision in a technology vacuum. If possible, the people who will be using the products should be involved in the decision-making process, so they can express opinions about how well the technology meets their needs and whether it will help them do their jobs better.
- Before purchasing a new technology and implementing it broadly across the enterprise, if feasible, test the product on a smaller group to understand how users will accept the technology. By doing this, IT executives can also become aware of any implementation problems that might arise and how to troubleshoot them.
In today’s “instant gratification” culture, it would be easy to just grab any new technology that catches your eye and try to use it. We know that companies market to individuals this way all the time. In reality though, marketers approach organizations the same way. Having a process by which to evaluate new technology is crucial to the actual success of the effective use of that technology. Otherwise the company is not only throwing away money, but it is taking time away from the important, strategic actions that should be taking place.
If there is no real benefit to the technology, then you are simply feeding your coins to a lost cause…
Architecture of the Future
The Enterprise Business Architecture, Part 3
So what will the Architecture of the Future look like? As much as it would be fun to explore futuristic architectural designs of buildings, that’s not what we are talking about. We know that over the last 10 years, the make-up of Enterprise Architecture has changed from process-oriented to business-outcome driven. This week’s topic has been specifically about the Enterprise Business Architecture, so what is the anticipation of change coming to this specific view of EA?
Gordon Barnett of Forrester wrote an article entitled “Business Architecture 2020 – Extending Beyond Organizational Boundaries” back in 2013. In 2016, he updated this article and it was renamed “Business Architecture 2020 – Evolving to Influence Business Strategy”. In this updated report, Barnett briefly summarizes a perspective of the future of Business Architecture, based on current trends in business and EA. The report includes 2 main takeaways (Barnett, 2016):
- Business Architecture will expand beyond Organizational Boundaries
- By 2020, Organizations will need different types of Business Architects
Let’s dig a little deeper into each of those topics.
Business Architecture will expand beyond Organizational Boundaries
As organizations have changed to be more global in nature, Business Architecture will need to reflect this shift as well. It is more common for organizations to have more dealings with external contractors, third-party vendors, partners, etc. Today’s Business Architect is focused on the internal organizational environment. However, tomorrows Business Architect will need need to shift their focus to the external environment which incorporates a much larger business ecosystem (Barnett, 2016). Barnett points out 2 key changes in this shift of focus:
External influence on strategic decisions will increase.
“Today, business strategy determines the market in which to compete and how the organization will win. External influence on business strategy is very limited. By 2020, as consumer and partner behaviors shift, organizations will need to extend their focus to the complete value-creation networks. External influence, particularly from customers, employees, and partners, will increase, and executive committees will need to react accordingly. BA focus will extend beyond the existing organization boundaries to include collaborating third parties, i.e., partners and customers. Organizations and BA leaders must understand the impact of these third parties on the agility of an organization’s strategy and on the delivery of value and experience to customers.”Partner influence on the strength of an organizations capabilities will grow.
For an organization to realize its mission requires a set of business capabilities: what an organization needs to satisfy its mission. Unless the organization undertakes a diversification strategy, the organization’s business capability needs will remain static. However, over time, the how, where, and who (the processes, information, technology, and people) will change to reflect the economic requirements and strategy of the organization.
In the future, the advancement of technology and innovation in business practices will broaden the ways in which partners influence the structure of an organization. Many organizations will focus only on their core business capabilities, with the noncore business capabilities provided by third parties; for example, an entity like ADP may provide payroll. This restructuring of the operating model will force BA to understand the maturity of these externally provided business capabilities and how they hinder or support the organization’s strategic intent.
Organizations will need Different Types of Business Architects
As the scope of Business Architecture widens, the individual skills of business architects will also need to grow. As more and more business architects become part of the normal business environment, there will be a need for business architects with varying skills, including many specializations. This may include focuses in specific business domains, corporate strategy or even analysis of industry trends. According to Barnett, this new breed of business analyst will have skills focused on (Barnett, 2016):
Strategic management. Many BA leaders state that their primary focus is strategic alignment or strategic direction/choice. However, very few BA leaders are actually at the table when firms are making strategic decisions. As 2020 approaches, the need for a deep understanding of an organization’s industry or market ecosystem will grow. Firms will need to answer a variety of questions, including determining the types of strategic relations needed to support business objectives. Ecosystem business architects will have opportunities to move into this space and join the strategic management group reporting directly to the CEO.
Analysis techniques and methods. Today, business architects have developed a core set of competencies to build internal blueprints of the organization. By 2020, as the scope of business architecture extends from a purely internal view of the organization to one that includes the organization’s operating environment, BA leaders will need to develop additional strategic and ecosystem analysis skills. This will involve mastering techniques such as political, economic, social, and technological (PEST) and customer-centric PEST (cPEST) analysis; Porter’s five forces; scenario analysis; persona analysis; journey maps; and other ecosystem analysis techniques.
Also, because the performance of an organization’s partners will help determine its performance, BA leaders will need to acquire skills to assess performance and dependency analysis, a form of systems thinking. In particular, business architects will need to answer questions such as these: What areas of the business performed outside of expectations? Why did this happen? Was this a one-off, or is it a trend?External relationship management. Today’s BA practices are recruiting business architects that have demonstrated mastery in soft skills, including communication, negotiation, facilitation, and diplomacy skills. In a world where business architecture extends beyond the boundaries of the organization, some stakeholders of business architecture will be external to the organization. Thus, business architects will need not only these soft skills but also external relationship management skills to address the different motivations and cultures of the external stakeholders.
Business model transformation and innovation. In the age of the customer and the world of digital business, executives will need the assistance of subject matter experts (SMEs) in the fields of customer life cycles and digital businesses. In particular, SME business architects will guide and influence strategy decisions that focus on delivering digitally enhanced experiences that add value in the context of their customers’ needs rather than purely on channel strategies. Firms will then be in a better position to combine digitally connected products and services to meet customer needs and deliver more value than the sum of their parts.
Barnett concludes his article with a few recommendations, of which they all primarily can be summarized as “start preparing your business architects now for the future.” If his predictions are accurate, then the investment now of additional training, organizational change, and the general extending of the business architecture practice will clearly pay off down the road.
References:
Barnett, Gordon. (2016). Business Architecture 2020 – Evolving to Influence Business Strategy. Forrester. Retrieved November 5, 2017 from https://www.forrester.com/report/Business+Architecture+2020+Evolving+To+Influence+Business+Strategy/-/E-RES95381
What’s in Your P4$$WØRD?
The Enterprise Security Architecture, Part 3
Image Source: Specops
I’ll just leave that image there so you can appreciate it’s profoundness…..
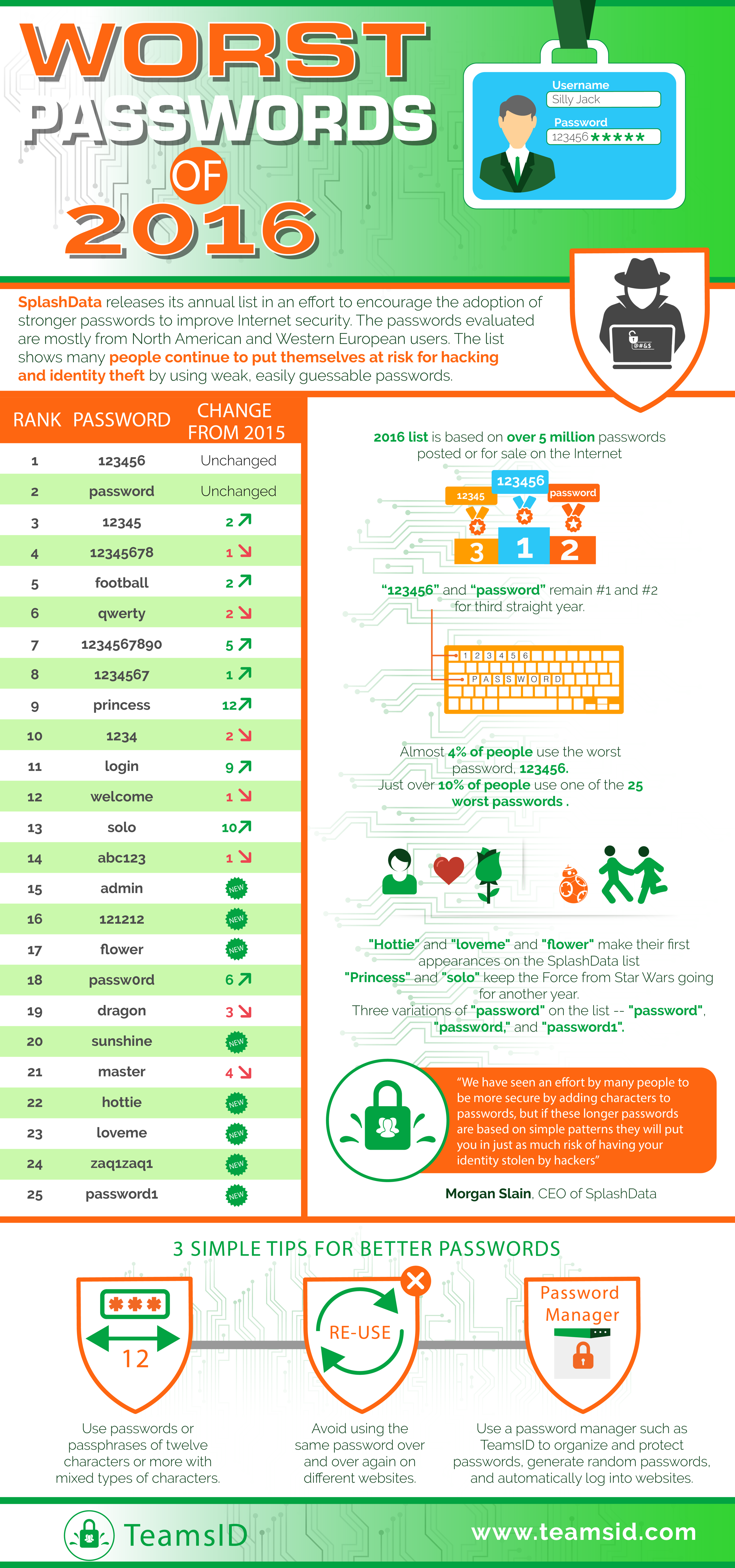
Any discussion about security needs to include our love/hate relationship with passwords. Passwords are one of the most basic security steps used in all aspects of cyber security. So why is it that there are so many people who have challenges with such a simple item? SplashData, a provider of password management tools, releases an annual list of the worst password people are actively using. This data comes from evaluation of leaked passwords from North America and Europe. This infographic is a little large, but I thought it worth viewing.
Image Source: TeamsID (SplashData)
So why do people have so many challenges with passwords? Specops, the source of the “underpants” photo above made this observation:
End users are wired to pick weak passwords – this goes back to cognitive psychology. As humans we are not equipped to retain meaningless information which means we make poor password choices. Either our passwords are just outright silly or they relate to our ego, our interests or something familiar. This is evident in the many common password lists out there, where password, 123456, football, master and monkey continue to make the top 20 most common passwords selected.
Instead of relying on end users to create secure passwords, which is unlikely, IT departments need to embrace better password policy practices that enforce more secure passwords by blocking the use of common dictionary words and enable more complex passwords by mixing different complexity rules (e.g. minimum of 10 characters with all four character sets or use passphrases that are longer than 20 characters).
This statement above regarding password complexity has been the standard operating procedure within IT and the business world for many years. Most of those practices originated back in the early 2000s from a document published by the National Institute of Standards and technology titled, “NIST Special Publication 800-63. Appendix A” (new 2017 version). We’ve all seen the standards that have been published with the “must contain at least 1 capital letter, 1 lowercase letter, 1 number and 1 special character.” And those passwords should be changed frequently.
Interestingly enough, the original author of the standard, Bill Burr, who is now retired, just recently was interviewed by the Wall Street Journal. In that interview, Burr admitted that he regretted his recommendations.
The problem is the advice ended up largely incorrect, Mr. Burr says. Change your password every 90 days? Most people make minor changes that are easy to guess, he laments. Changing Pa55word!1 to Pa55word!2 doesn’t keep the hackers at bay. Also off the mark: demanding a letter, number, uppercase letter and special character such as an exclamation point or question mark—a finger-twisting requirement.
In June, the NIST did a complete rewrite of the standard with a completely different set of recommendations. The goal was to make obscure passwords that are easy for the user to remember, but more challenging for hackers or bots to crack. Password expiration is no longer recommended unless there is evidence that your password was stolen.
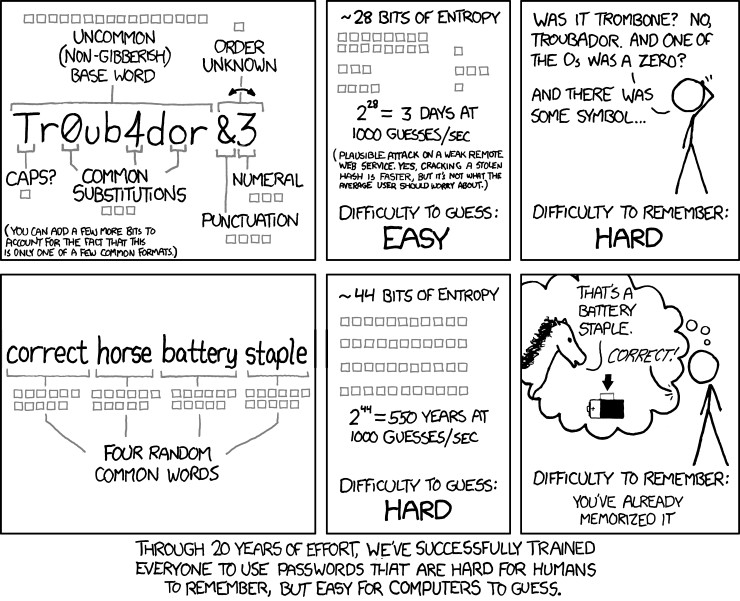
Back in 2011, this exact sentiment was expressed by cartoonist Randall Munroe, the author of the comic xkcd. “Through 20 years of effort, we have correctly trained everyone to use passwords that are hard for humans to remember, but easy for computers to guess.”
Now, how long will it be before this common sense change will filter out into the business world…?
Risky Business
The Enterprise Technology Architecture, Part 3
In technology, just as in business in general or even life, there are risks that we all take. Whether it’s skydiving, investing in a new startup or implementing new technology, there are always risk that need to be evaluated and weighed. Each area of society has it’s own specific risks, and within the technology field, it is no different. Risks that are common with technology tend to fit into these categories:
- Scalability – Will my technology be able to handle the scope that I need now as well as grow to fit the scope in the future?
- Longevity (Vendor Defocus) – Will my technology continue to be efficient and supported in the future or will it need to be quickly replaced by new technology?
- Failure to meet Expectations (Technology Death) – Will new technology I acquire actually meet my needs?
- Lack of Support – Will the vendor/developer be able to support my needs?
- Lack of Expertise – Are there resources available to acquire which can internally support the technology for the long-term?
- Cost of Technology – Will the cost of buying and using technology becomes unaffordable?
- Data Integrity & Security – How do I keep my data safe and prevent data corruption?
- General Technology Security – Aside from data, how do I keep the rest of my technology secure? This includes malware and viruses.
- Redundancy – Do I have the necessary backup systems in place to keep my business functioning?
- New Technology Adoption – How do I know when to implement something new? What will be the positive and negative outcomes of the adoption?
As I talked about previously in How Do You Adopt?, the adoption of innovation breaks down into 5 basic categories:
- Innovators – 2.5% of the population.
- Early Adopters – 13.5% of the population.
- Early Majority – 34% of the population.
- Late Majority – 34% of the population.
- Laggards – 16% of the population.
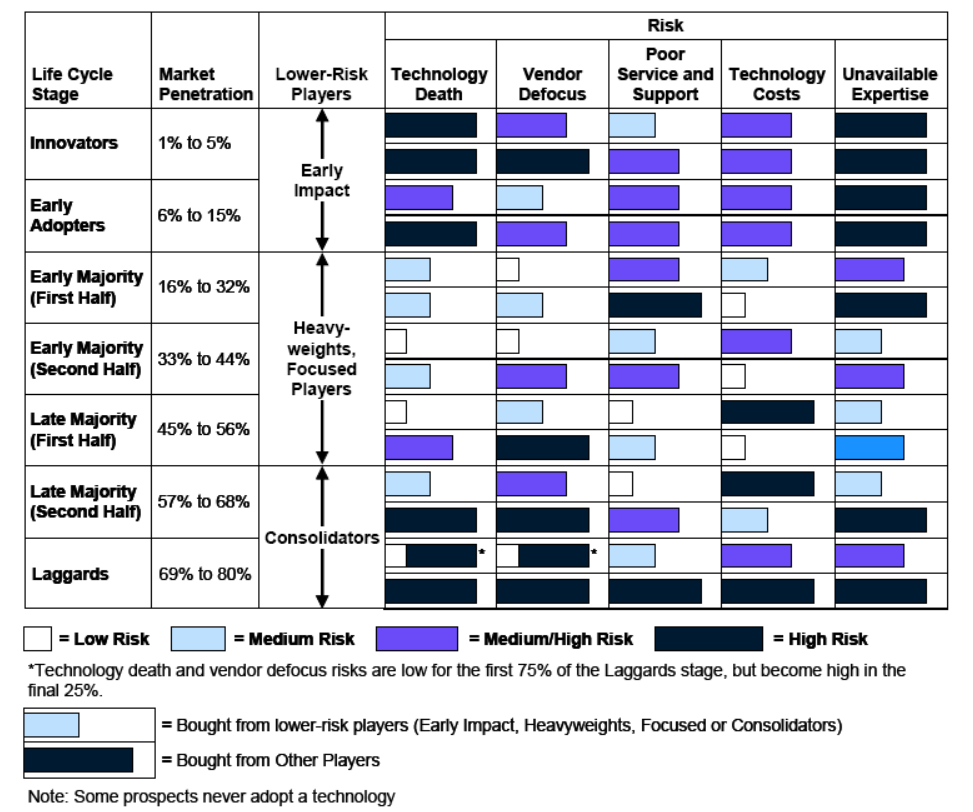
As pointed out by Mike Blechar of Gartner, the technology risk level is directly dependent on the type of adopter involved (Blechar, 2006). This is also directly related to the vendor from which the technology is purchased. Blechar used 5 similar categories to differentiate vendors which correspond to the same category if adopters:
- Early Impact Players
- Other Players
- Heavyweights
- Focused Players
- Consolidators
Bechar goes on to detail how adopters and vendors interact:
During the technology’s first two life cycle stages (Innovators and Early Adopters), the vendors in the market will be Early Impact Players and Other Players. As the market matures and technology enters the Early Majority stage of the life cycle, vendors that are Early Impact Players transform into Heavyweights or Focused Players. Some Other Players will disappear during the Early Majority stage, and a few may be able to become Focused Players or Heavyweights. As the Early Majority stage progresses, and to the end of the first half of the Late Majority stage, vendors may move between different classifications. Heavyweights may become Focused Players or disappear, and Focused Players may become Heavyweights or disappear. The risks of buying from Other Players that survive to the end of the first half of the Late Majority stage will remain high.
Another change happens as the technology moves into the second half of the Late Majority stage. By now, the market is approaching saturation and is beginning to consolidate. Some vendors that are Heavyweights and Focused Players will exit the market (particularly during the final Laggards stage of the technology life cycle); other vendors will be acquired or will merge to become Consolidators. As the technology life cycle draws to a close, the majority of vendors left in the market will be Consolidators. These will be the vendors that have the largest and most stable maintenance revenue and, in terms of technology risk, are the “best bets.” The technology risks associated with Other Players that survive into the second half of the Late Majority and Laggard stages are now at their highest.
The severity of the risks will change for the vendors as the technology life cycle of adoption progresses. Understanding how the risk levels change throughout the technology life-cycle can help potentially mitigate those risks by proactively addressing them.
Image Source: Blechar, 2006
References:
Blechar, Mike. (2006). Managing Technology Life Cycle Risks. (G00142109). Gartner.
With Great Power Comes Great Responsibility
The Enterprise Data Architecture, Part 3
Every year, we face challenge after challenge regarding data security. Whether it’s personal identity theft, corporate data hacking, ransomware or industrial espionage, it seems like for every step forward, we take two-three steps backwards. This has a large impact not only on private consumers, but on the business world in general.
For consumers, the biggest issue being dealt with is Identity Fraud. With the increasing amount of Identity theft & fraud, consumers are facing more and more challenges to keep their personal data safe. More and more data is being collected from the consumer, from browsing habits to shopping trends. Additionally, critical personal information such as credit card information, phone numbers, address, or even occasionally social security numbers are being used on various online websites. Let’s not even start a discussion about the credit card skimmers at various retailers….
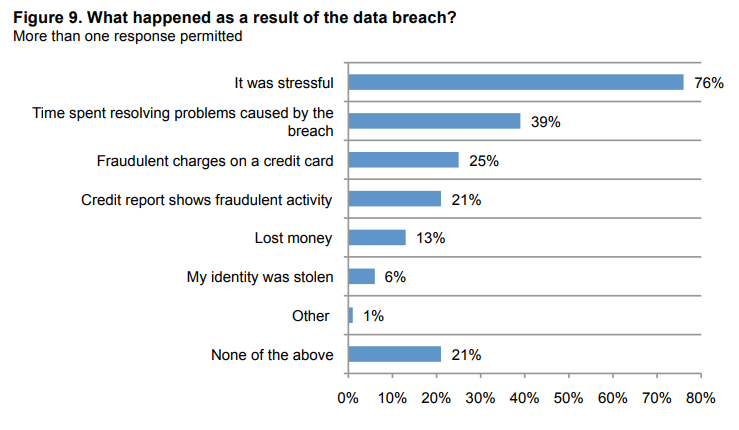
And what happens after your personal data has been stolen…?
Image Source: Ponemon Institute
On the business side, it appears that no one is safe. With the recent hack of Equifax, we have seen tremendous amounts of data stolen that could be devastating to consumers. A reported 143 million people’s data was taken, potentially including Social Security numbers. And the worse part? None of us even gave Equifax permission to have our data to begin with. The list of hacks for 2017, according to ZDNet, is frightening:
- Equifax – 143 million accounts
- Verizon – 14+ million accounts
- Bell Canada – 1.9 million accounts
- Edmodo – 77 million accounts
- Handbrake (video encoder software for Mac) – unknown number of users
- Wonga – 270 thousand accounts
- Wannacry ransomware – 200 thousand computers
- Sabre – thousands of business customers
- Virgin America
- Cellebrite
- Cloudfare
- iCloud
- TSA
- OneLogin
- US Air Force
The list could go on. We live in a time where data is everywhere. This is the reality of Big Data. Regardless of whether it’s your personal data or business data, it is stored somewhere, and it is potentially susceptible to to unwanted exposure. We know that hackers are going to try their best to get to that data. So what are the real challenges for the security of Big Data? And what can we do to make it more secure? According to Data Center Knowledge, here is a list of the top 9 Big Data Security challenges, and potential ways the security could be improved.
Big Data Security Challenges:
- Most distributed systems’ computations have only a single level of protection, which is not recommended.
- Non-relational databases (NoSQL) are actively evolving, making it difficult for security solutions to keep up with demand.
- Automated data transfer requires additional security measures, which are often not available.
- When a system receives a large amount of information, it should be validated to remain trustworthy and accurate; this practice doesn’t always occur, however.
- Unethical IT specialists practicing information mining can gather personal data without asking users for permission or notifying them.
- Access control encryption and connections security can become dated and inaccessible to the IT specialists who rely on it.
- Some organizations cannot – or do not – institute access controls to divide the level of confidentiality within the company.
- Recommended detailed audits are not routinely performed on Big Data due to the huge amount of information involved.
- Due to the size of Big Data, its origins are not consistently monitored and tracked.
How can Big Data Security be Improved?
- The continued expansion of the antivirus industry.
- Focus on application security, rather than device security.
- Isolate devices and servers containing critical data.
- Introduce real-time security information and event management.
- Provide reactive and proactive protection.
As stated by James Norrie, dean of the Graham School of Business at York College of Pennsylvania, “Big companies made big data happen. Now, ‘big security’ must follow, despite the costs. Regulators and legislators need to remind them through coordinated actions that they can spend it now to protect us all in advance or pay it later in big fines when they don’t. But either way, they are going to pay. Otherwise, the only ones paying will be consumers.”