The Enterprise Security Architecture, Part 2
An XT-4200 Post & Beam Gate providing a vehicle security access point (American Security Today)
So how do we go about creating the Security Architecture? What needs to be included and how do we measure its’ effectiveness? One thing is clear. The security of yesterday is no longer adequate for the risks of today.
In March of this year, the Ponemon Institute released a study named “The Need for a New IT Security Architecture“. The report surveyed more than 4000 IT and security experts from around the world. An analysis of this report by security firm Centrify discussed the findings that concern risks created by cyber-crime, employee negligence and organizational dysfunction and the technologies respondents believe are most effective at dealing with these risks (Gibson, 2017):
Outdated Security Solutions
Organizations are concerned they will not be able to manage emerging risks because of outdated security solutions.
- 69 percent of respondents say their organization’s existing security solutions are outdated and inadequate.
- What is needed, according to 74 percent of respondents, is a new IT security framework to improve security posture and reduce risk.
- A new strategy is important in order to manage potential risks from the Internet of Things (75 percent of respondents).
Trends in IT Security Risk
The findings reveal that most risks, with the exception of globalization of the workforce, are very significant. The top cybercrime risks are:
- Nation state attackers (80 percent of respondents)
- Breaches involving high-value information such intellectual property and trade secrets (79 percent of respondents)
- Malicious or criminal insiders (76 percent of respondents)
- Cyber warfare or cyber terrorism (76 percent of respondents)
An Evolving Workplace
The workplace is changing and so are the human factor risks. While 81 percent of respondents are concerned about the inability to hire and retain security staff with knowledge and credential, employee behaviors are creating risks that pose a significant risk.
- Employee complacency about security (74 percent of respondents)
- Lack of employee awareness of security practices (72 percent of respondents)
- The inability to control employees’ devices and apps (71 percent of respondents)
Complexity and legacy drag is a familiar problem that leads to high cost and contributes to shortage of competent professionals. Complexity and outdated security architectures create risk and weaken security posture.
Complexity is a Security Risk
Complexity of business and IT operations is a significant security risk. According to 83 percent of respondents, too much complexity is making organizations more vulnerable to security threats. Other trends are the growth of data assets (78 percent of respondents) and the process of integrating third parties into internal networks and applications.
Complexity is created in part by security vendors, who for decades have sold point solutions into IT environments with little thought to integration, maintenance and the cost of expertise to maintain their products.
Important Technologies for IT
Certain technologies are needed for a new IT security infrastructure.
Respondents believe their organizations’ IT security solutions are outdated and failing to mitigate the risks of cyber-crime, employee behavior and organizational problems. The most important technologies are:
- Identity & access management (78 percent of respondents)
- Machine learning (77 percent of respondents)
- Configuration & log management (76 percent of respondents)
An Architecture to Secure Identity in a Boundaryless Hybrid Environment
As reflected in the concerns of survey respondents, aging security infrastructure and point products create complexity, increase cost and risk and contribute to the critical security staff shortages. New security architectures that protect digital identity of all users across boundary-less hybrid environments and myriad devices are required.
We know, according to Verizon’s 2016 Data Breach Investigations Report, that the #1 cause of data breach is compromised user identity. We know that eliminating multiple identities and passwords, combined with least-access least-privilege policy and multi-factor authentication (MFA) everywhere is one effective way to contain and prevent attackers from gaining access to critical resources.
So with all these concerns, what are the necessary elements in a contemporary Security Architecture that not only protects users and applications, but improves productivity and security? According to Gibson, they can be summarized as:
- A modern security architecture is purpose-built, based on a goal to protect digital identity for all users across hybrid cloud and mobile environments.
- It’s built on a single code-base, with API’s SDKS’s that support security industry standards and integrates with other technologies.
- It’s constantly evolving.
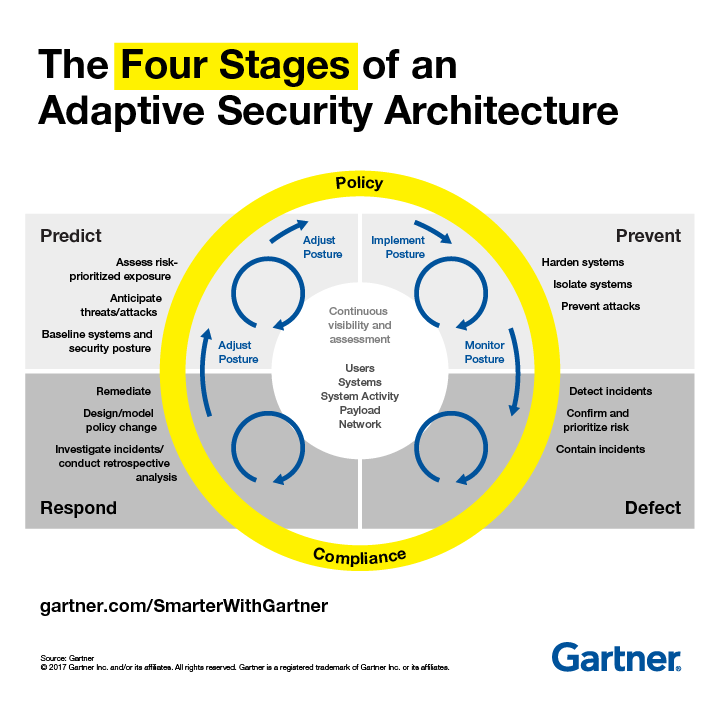
Rob van der Meulen of Gartner also recently posted a similar conclusion in a security article titled “Build Adaptive Security Architecture Into Your Organization“.
Many enterprise IT security teams spend much of their time focused on preventing a cyberattack. In doing so, they have implemented a “incident response” mindset rather than a “continuous response” where systems are assumed to be compromised and require continuous monitoring and remediation.
The adaptive security architecture is a useful framework to help organisations classify existing and potential security investments to ensure that there is a balanced approach to security investments. Rather than allowing the “hot” security startup of the day to define security investments, Gartner recommends that security organizations evaluate their existing investments and competencies to determine where they are deficient.
Digital business is built upon an intelligent mesh of devices, software, processes and people. This means an ever more complex world for security, demanding a continuous, contextual and coordinated approach.
The article went on to describe 4 stages of this new “Adaptive Security Architecture”
This concept of continuous improvement and adaptation is not new in the business world. Applying similar principles to a Security Architecture has rapidly evolved into the only way to stay on top of the ever changing world of today’s security risks.
References:
Gibson, Mark. (February, 2017). Ponemon 2017 Report: The Need for a New IT Security Architecture. Centrify. Retrieved October, 13, 2017 from https://blog.centrify.com/ponemon-2017-report/